
What is the Significance of Firewall Policy in ensuring Network Security?
The Significance of Firewall Policy: Ensuring Network Security
Editor's Notes: "The Significance of Firewall Policy: Ensuring Network Security" has been published today. This topic is significant to read as it provides insights into securing your network.
We have analyzed and dug into information. The result is, we have put together this guide to help you make the right decisions.
Key Differences
| Key | Value |
|---|---|
| Importance | Security |
| Benefits | Protection from threats |
Main Article Topics
FAQ
This section provides answers to frequently asked questions (FAQs) that clarify the significance of firewall policy in maintaining network security.
Cyber Security – Educatifu Technologies - Source educatifu.com
Question 1: What is a firewall policy, and why is it crucial?
A firewall policy defines a set of rules that determine how a firewall handles incoming and outgoing network traffic. It acts as a security mechanism, protecting networks from unauthorized access and malicious attacks. By enforcing these rules, the policy helps prevent network breaches, data loss, and system compromise.
Question 2: How does a firewall policy protect network security?
Firewall policies are essential for network security. They allow organizations to control and restrict network access, ensuring that only authorized entities can enter or exit the network. These policies also define specific criteria for traffic inspection, such as port numbers and protocols, to block malicious traffic and prevent unauthorized access.
Question 3: What are the key components of a firewall policy?
Effective firewall policies include rules, traffic inspection criteria, and exception handling mechanisms. Rules define allowed and denied connections, while traffic inspection criteria determine how traffic is filtered. Exception handling mechanisms ensure that legitimate traffic is not blocked, such as traffic from trusted sources or for specific business purposes.
Question 4: How can organizations improve their firewall policy effectiveness?
To enhance firewall policy effectiveness, organizations should regularly review and update policies to address emerging threats. They should also implement intrusion detection and prevention systems (IPS/IDS) to complement firewall policies and enhance overall security.
Question 5: What are the best practices for managing firewall policies?
Best practices include documenting policies clearly, testing them thoroughly, and implementing automated tools for policy management. Organizations should also conduct regular security audits to identify vulnerabilities and ensure that policies remain aligned with security requirements.
Question 6: What are the consequences of neglecting firewall policy management?
Neglecting firewall policy management can have severe consequences. Organizations risk exposing their networks to unauthorized access, data breaches, and cyberattacks. Unpatched vulnerabilities and outdated policies provide opportunities for attackers to exploit weaknesses and compromise network security.
Remember, firewall policies are a critical component of a comprehensive network security strategy. By implementing effective policies and adhering to best practices, organizations can significantly enhance their defenses against cyber threats and safeguard their sensitive data.
Conclusion: Firewall policy management plays a fundamental role in safeguarding networks from cyber threats. By understanding the significance of firewall policies, implementing them effectively, and following best practices, organizations can strengthen their security posture and protect their valuable information assets.
Tips to Enhance Firewall Policy Effectiveness
Firewall policies are integral to safeguarding networks from unauthorized access and cybersecurity threats. The Significance Of Firewall Policy: Ensuring Network Security, implementing robust policies is essential for organizations to protect their IT infrastructure and data.
Tip 1: Define a Clear Policy:
Establish a comprehensive firewall policy outlining the rules for network access, including permitted protocols, ports, and IP addresses. Ensure the policy aligns with the organization's security requirements and regulatory compliance needs.
Tip 2: Regularly Review and Update:
Firewalls should be reviewed regularly to ensure they are up-to-date with the latest threat landscape. Policies should be modified as necessary to address evolving security risks, such as zero-day vulnerabilities and malware attacks.
Tip 3: Implement Zone-Based Segmentation:
Divide the network into logical zones based on security requirements, such as internal, external, and DMZ. Configure firewall rules to restrict traffic flow between zones, isolating sensitive assets from potential threats.
Tip 4: Leverage Intrusion Prevention Systems:
In addition to basic firewall rules, implement intrusion prevention systems (IPS) to detect and block malicious traffic. IPS monitors network traffic for known attack signatures and takes proactive measures to prevent breaches.
Tip 5: Conduct Penetration Testing and Simulation:
Regularly perform penetration testing and simulations to evaluate the effectiveness of firewall policies. These exercises help identify security gaps and weaknesses that can be addressed to enhance overall network resilience.
By adhering to these tips, organizations can strengthen their firewall policies, ensuring optimal network security and mitigating the risk of data breaches and cyber threats.
The Significance Of Firewall Policy: Ensuring Network Security
A firewall policy is a set of rules that dictates how a firewall should handle network traffic. It is an essential component of any network security strategy, as it provides the first line of defense against unauthorized access to a network.
- Access Control: Determines who can access the network and what resources they can access.
- Logging and Monitoring: Records and tracks all network traffic, providing visibility into potential security threats.
- Intrusion Prevention: Blocks malicious traffic and prevents unauthorized access attempts.
- Compliance: Helps organizations meet regulatory requirements and industry standards.
- Network Segmentation: Divides the network into smaller, more manageable segments, limiting the spread of threats.
- Threat Intelligence: Updates firewall rules based on the latest threat intelligence, providing protection against emerging threats.

WPP Issues New Policy ‘Ensuring the Safe Consumption of Alcohol’ at - Source www.adweek.com
Firewall policies are essential for maintaining the security of any network. They provide a comprehensive approach to network protection, addressing various dimensions of security, from access control to threat intelligence. By implementing a robust firewall policy, organizations can significantly reduce the risk of unauthorized access, data breaches, and other network security threats.

Comptia Network+ Tutorial: Module 05, Part 04: Wireless Network Threats - Source gotowebsecurity.com
The Significance Of Firewall Policy: Ensuring Network Security
A firewall policy is a set of rules that define how a firewall operates. It determines which traffic is allowed to enter and exit the network, and which traffic is blocked. A well-configured firewall policy can help to protect the network from unauthorized access, denial-of-service attacks, and other threats.
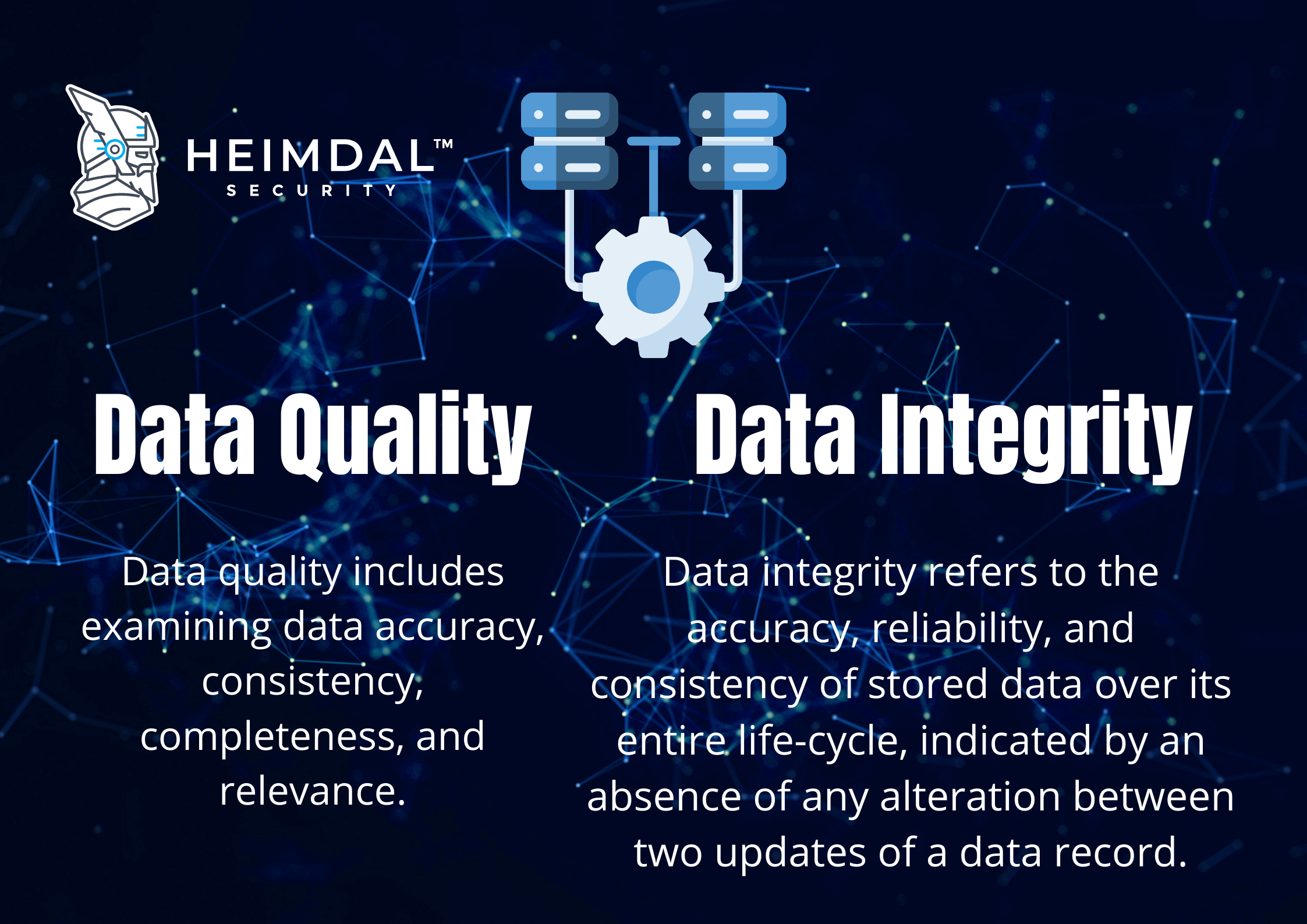
Ensuring Data Integrity in Cloud Services: Best Practices & Techniques - Source nhuaqt.com
Firewall policies are an essential part of any network security strategy. They can help to protect the network from a wide range of threats, and they can be customized to meet the specific needs of the organization.
There are a number of different types of firewall policies, each with its own advantages and disadvantages. The most common type of firewall policy is the stateful firewall policy. A stateful firewall policy tracks the state of each connection, and it only allows traffic that is part of an established connection. This type of firewall policy is very effective at preventing unauthorized access to the network, but it can be more difficult to configure and manage.
Another type of firewall policy is the packet filtering firewall policy. A packet filtering firewall policy examines each packet of data that enters or exits the network, and it only allows traffic that meets certain criteria. This type of firewall policy is less effective at preventing unauthorized access to the network than a stateful firewall policy, but it is easier to configure and manage.
The best type of firewall policy for an organization will depend on the specific needs of the organization. It is important to consider the size of the network, the types of threats that the network is facing, and the resources that are available to manage the firewall.
Here are some tips for creating a firewall policy:
- Identify the assets that need to be protected.
- Determine the threats that the network is facing.
- Choose the type of firewall policy that is best suited to the needs of the organization.
- Configure the firewall policy according to the manufacturer's instructions.
- Monitor the firewall policy and make changes as needed.
By following these tips, organizations can create a firewall policy that will help to protect the network from a wide range of threats.
Recomended Posts


